vRealize Network Insight (vRNI) is most famous for its ability to help you with getting insight into your virtual traffic flows. Using that information you have all you need to configure micro-segmentation. vRNI is much more than that though and this post is the first of a series going into depth of some of the awesome capabilities of vRNI.
All Your Firewall Rules Belong to vRNI
One thing vRNI does, is inventory all the network configuration of the data sources (devices such as switches, routers, firewalls) you add to it. Among those data sources, NSX and Palo Alto Network devices can be added to vRNI for firewall rule discovery.
The discovery process combines the NSX firewall rules and the Palo Alto firewall rules into one view. You just look up a VM, open up the Firewall rules window and there they are: all the firewall rules that apply to that specific VM. No long list of every firewall rule that exists. No manually filtering of a long list of firewall rules on IP or IP range to get to the rules that apply to a specific VM.
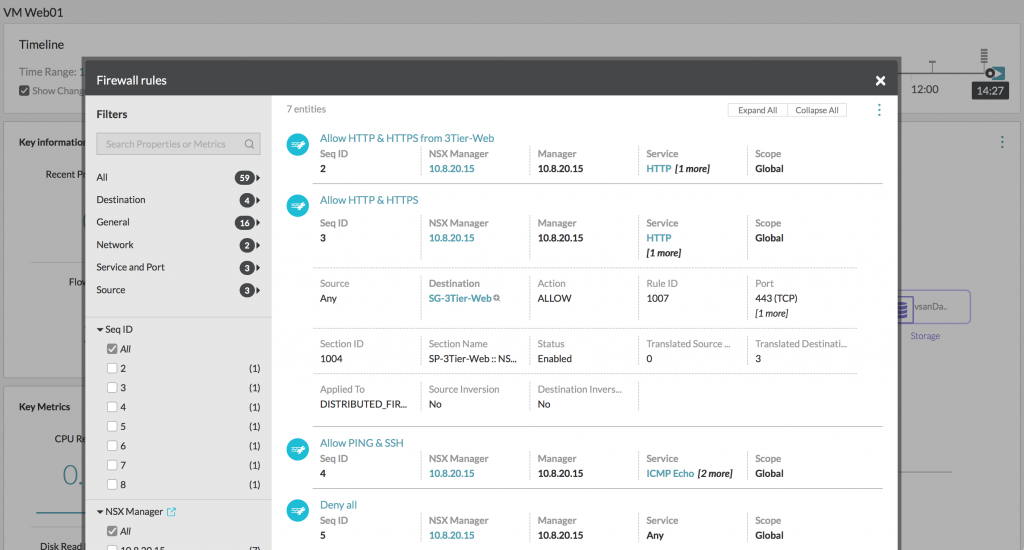 |
| * Screenshot from my testlab without a physical firewall, so only NSX firewall rules. |
Searching Firewall Rules
One of the best features of vRNI is its natural language search engine. You can type out searches like you do in Google, the search bar will give you available keywords (currently 93!) as a hint and the total available types of searches you can do are pretty much unlimited. Here are a few examples of keywords: VM, Host, VLAN, Datastore, Palo Alto Zone, NSX Security Group, Router, Switch, Firewall Rule. Let’s focus on the last one; Firewall Rule.
With a search, you can also add modifiers like ‘where’, ‘and’ & ‘or’. This means you can build search queries like the few examples below:
- Firewall Rule Where (Port = 80 or Port = 443) And Action = Allow
- Firewall Rule Where Destination Vm = ‘App02’
- Firewall Rule Where Source = ‘internet’ And Port = 443
- Firewall Rule Where Destination = ‘internet’ And Port = 1433
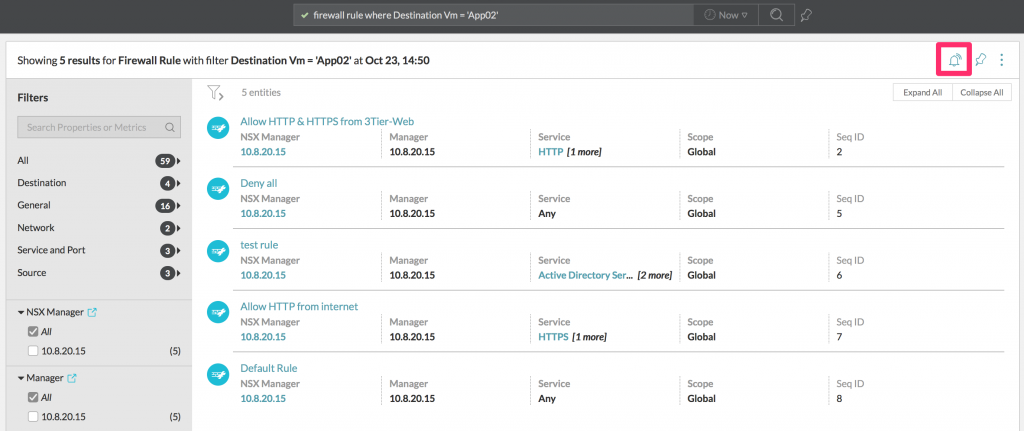 |
| * The circled bell will be explained in the notifications section. |
Keyword “Internet”
Notice the last two of the above examples, where the source and destination were used to say ‘internet’. This is a collection keyword of any IP address that is not in the local network (private IP ranges and the manually entered “Datacenter Public IPs” in the settings). If your firewall rules contain either public IP addresses/ranges or “any” – it will match the keyword internet.
This makes it possible to search any firewall rule that will allow access from the outside to the inside. Let’s think about this for a moment. With a putting one line in the search engine, you are able to get all firewall rules that allow network connectivity from the internet to the internal network and see the VMs that those rules apply to. In one search.
NSX Security Group Membership Changes
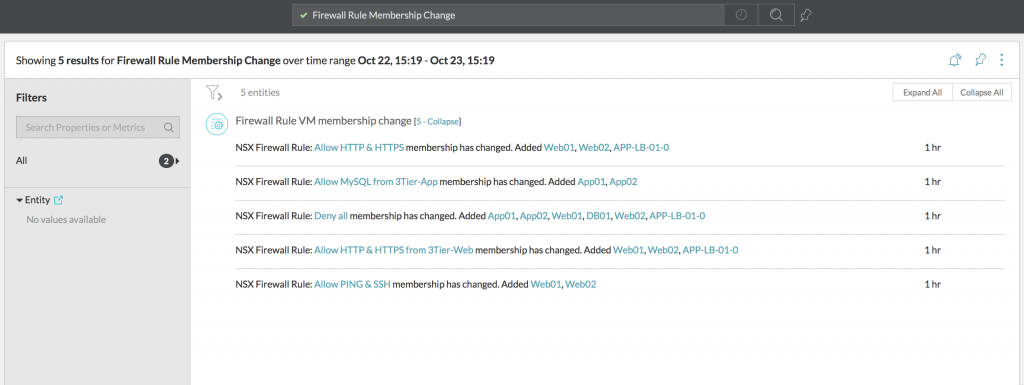
NSX Security Groups and NSX Security Policies are concepts that NSX introduced to dynamically protect VMs based on properties of the VM itself. With Security Groups, VMs can be automatically protected and you don’t have to worry about manually configuring firewall rules for the VMs that are deployed. This dynamically created security domain can be very fluid and VMs can enter and leave the domain as easy as modifying the VM in vCenter or with a single API call to NSX.
Because NSX itself is a ‘in the moment’ platform and gives integrations the possibility to keep a historic record of changes inside the NSX environment. vRNI takes advantage of that possibility and gives you the ability to search for an overview of changes within Security Groups. Every time a VM joins or leaves a Security Group, it’ll create an audit trail which you can follow.
Notifications on Changes
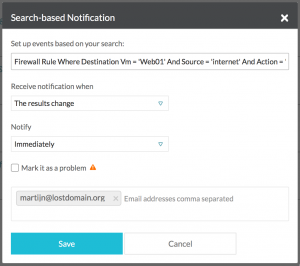
On any search you do in the search engine, you can configure a notification on the results of that search. For example, if you do a search on all firewall rules that allows network connectivity from the internet to a specific VM or a collection of VMs and want to be notified on any changes to those firewall rules. Good for security compliance or just keeping an eye on your firewall rules.
Create a notification by simply doing a search and using the alarm bell icon in the top right. This will open up a new window which will allow you to configure the notification. You can choose whether to receive a notification when the search results change, or when there are no results anymore (good if you want to keep a certain ruleset in place). You can also select whether you want an instant notification, an hourly or a daily digest. And from vRNI 3.1, you can also configure destination emails to send the notifications through email instead of just the web interface.
Conclusion
Due to the data driven nature of vRealize Network Insight, it can see the entire security stack. Because it can see the entire security stack, you can do a lot of cool stuff with the search engine and the notifications. When set up properly and thought out, vRNI can ensure compliancy in security policies and provide audit trails.

Leave a Reply