VCIX-NV Objective 3.2 – Configure and Manage Logical Virtual Private Networks (VPNs)
This post is part of my VMware VCIX-NV Study Guide and covers the Virtual Private Network connection (VPNs) options inside VMware NSX.
Documentation
Index
- Enable/Disable IPSec VPN service
- Configure global IPSec VPN parameters
- Generate a Certificate Signing Request (CSR)
- Enable and configure logging
- Implement Network Access SSL VPN-Plus
- Implement Web Access SSL VPN-Plus
- Enable/Disable L2 VPN
- Add and configure a L2 VPN server
- Add and configure a L2 VPN client
Virtual Private Networks The NSX Edge Services Gateway allow you to set up VPN tunnels between the ESG and any VPN/IPsec capable device. There are a few different kinds of VPN that the ESG supports: regular IPsec VPN, L2 (Layer-2) VPNs to bridge networks and SSL-VPN for endusers.
Everyone knows regular the IPsec VPN, to create a secure connection between two sites and route the internal subnets between those two sites. L2 VPNs are relatively new though, allow for some pretty great migration scenarios or a way to effortlessly burst your computing to another site (cloud hoster) using the same subnet for application requirement reasons. SSL-VPN on the other hand is a perfect way of allowing endusers to connect over SSL (https), which is allowed in 99.9999% of the public networks, to create a secure connection between the location they’re on (public coffee shop network) and the network inside NSX where their data lives.
Enable/Disable IPSec VPN service
Requirements:
- Existing NSX Edge Services Gateway.
VMware Documentation: Enable IPSec VPN Service
Before configuring IPsec VPN tunnels, you need to enable the IPsec service. This is probably the most difficult task in the entire VCIX-NV blueprint. Hang on to your socks.
Enable the IPsec VPN service
- Login to your vSphere Web Client.
- Navigate to “Networking & Security” and select the “NSX Edges” menu.
- Choose the NSX Edge you want to modify and select the “Manage” tab.
- Then select the “VPN” sub-tab and select the “IPsec VPN” sub-menu.
- Once there, click the “Enable” button.
- Click the “Publish changes” button that appears.
Configure global IPSec VPN parameters
Requirements:
- Existing NSX Edge Services Gateway.
VMware Documentation: Specify Global IPSec VPN Configuration
Global IPsec VPN parameters consists of a default Pre-Shared Key (PSK) and the SSL certificate the service uses for certificate authentication.
Configure default IPsec VPN settings
- Login to your vSphere Web Client.
- Navigate to “Networking & Security” and select the “NSX Edges” menu.
- Choose the NSX Edge you want to modify and select the “Manage” tab.
- Then select the “VPN” sub-tab and select the “IPsec VPN” sub-menu.
- Once there, click the “Configure” link to open the global settings.
- In the popup window, configure the default PSK and SSL certificate and click “OK” when done.
- Finally click the “Publish Changes” button which appears.
Generate a Certificate Signing Request (CSR)
Requirements:
- Existing NSX Edge Services Gateway.
VMware Documentation: Working with Certificates
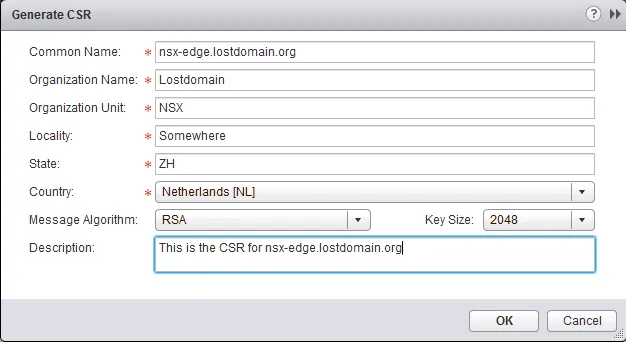
The NSX Edges can use SSL certificates for a bunch of things (load balancing, IPsec VPN authentication and SSL-VPN website authenticity). I’m not going to dive in to the workings of SSL certificates, there are a lot of resources on that. To start the SSL certificate signing process, you need a Certificate Signing Request. Here’s how to create a CSR in the NSX Edge.
Creating a CSR
- Login to your vSphere Web Client.
- Navigate to “Networking & Security” and select the “NSX Edges” menu.
- Choose the NSX Edge you want to modify and select the “Manage” tab.
- Then select the “Settings” sub-tab and select the “Certificates” sub-menu.
- Once there, click the “Action” menu and select “Generate CSR”.
- In the popup window, enter all the required certificate details (and take note of the details) and click “OK” when you’re done.
- When the CSR is generated you will be returned to the “Certificates” screen and you can select the CSR and copy the “PEM Encoding” for use in the certificate request you need to file with your private Certificate Authority (CA) or a public CA.
Enable and configure logging
Requirements:
- Existing NSX Edge Services Gateway.
VMware Documentation: Enable Logging for IPSec VPN
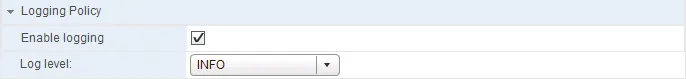
Setting up VPNs between different vendors can be tricky. Logging can save your day there and you would be wise to enable logging at least during setup.
Enabling Logging
- Login to your vSphere Web Client.
- Navigate to “Networking & Security” and select the “NSX Edges” menu.
- Choose the NSX Edge you want to modify and select the “Manage” tab.
- Then select the “VPN” sub-tab and select the “IPsec VPN” sub-menu.
- Expand “Logging Policy” and tick “Enable logging” and set a logging level.
- Click the “Publish Changes” button that appears.
Implement Network Access SSL VPN-Plus
Requirements:
- Existing NSX Edge Services Gateway.
VMware Documentation: Configure Network Access SSL VPN-Plus
SSL VPN-Plus inside the NSX Edge Services Gateway will allow you to grant remote users access to the virtual network through a SSL-VPN tunnel. This runs over https and is allowed over most public networks, so the ideal way to set up a VPN where-ever your users are. To implement SSL VPN-Plus you have to go through a few steps, which are listed below.
Make the ESG listen on an interface
- Login to your vSphere Web Client.
- Navigate to “Networking & Security” and select the “NSX Edges” menu.
- Choose the NSX Edge you want to modify and select the “Manage” tab.
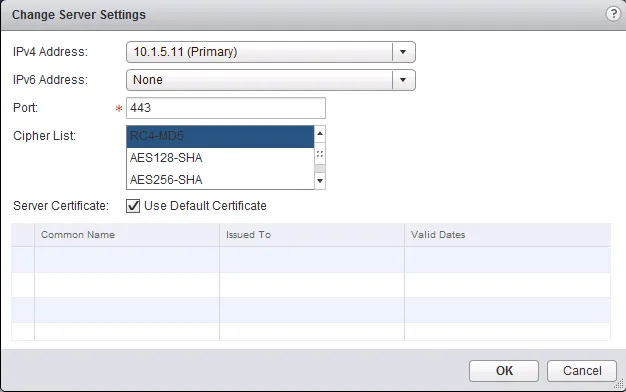
- Then select the “SSL VPN-Plus” sub-tab and select the “Server Settings” sub-menu.
- Click the “Change” button. Then in the popup window select the IPv4 Address (interface), optional IPv6 interface and the port (default 443).
- Also optionally select a server certificate to use for the SSL connection. Click “OK” when you’re done.
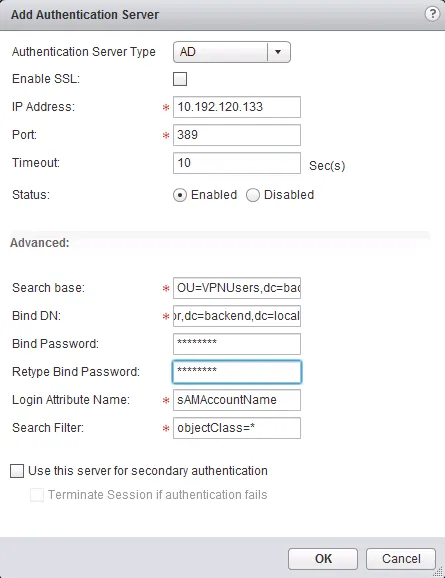
After setting the listening IP address, you need to configure an authentication server. This is where the ESG will perform the user authentication on and it can be of the following types: Active Directory (AD), LDAP, RADIUS, RSA-ACE and LOCAL authentication. The LOCAL server type will keep the authentication locally on the ESG and you will need to submit accounts to the ESG interface. In this example, I’ll be using an active directory server.
Add an authentication server
- Move from the “Server Settings” sub-menu to the “Authentication” sub-menu.
- Then select the “Load Balancer” sub-tab and select the “Global Configuration” sub-menu.
- Click the ”+” icon to add an authentication server.
- Select the server type and enter all details needed. In the case of an AD server: IP address, LDAP port, LDAP Search base, Bind DN (username), Bind Password and the login attribute and search filter (default will be okay there).
- If you selected “LOCAL” as the authentication type, you’ll need to head over to the “Users” sub-menu and add yourself a user to test with.
Next up is to add an IP pool where the connected users will get their VPN IP addresses from.
Add an IP Pool
- Move from the “Authentication” sub-menu to the “IP Pool” sub-menu.
- Click the ”+” icon at the top left to start adding an IP pool.
- In the popup window, enter the “IP Range”, its “Netmask” and the “Gateway” address. Add an optional description, DNS servers and suffix and a WINS server (all optional).
- Click “OK” to add it.
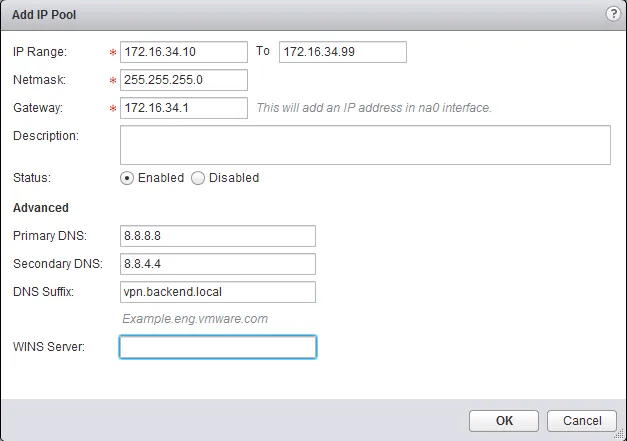
After giving the users an IP address from that IP Pool you just created, you need to determine what IP networks the user needs to be able to reach over the VPN. You can also insert exceptions for networks that need to routed over the internet instead of through the tunnel, which is handy if you decide to route everything over the tunnel and want to add exceptions for internet addresses.
Add a Private Network
- Move from the “IP Pool” sub-menu to the “Private Networks” sub-menu.
- Click the ”+” icon at the top left to start adding a private network.
- In the popup window, the details of the subnet you want to include or except in or from the VPN tunnel. In the example, I’m routing the CRM Servers over the VPN tunnel. Click “OK” when you’re done.
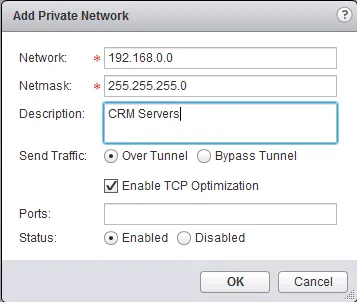
The last thing to do before enabling the SSL VPN-Plus service is to add an “Installation package”. The VMware NSX SSL-VPN client is delivered in an installer download, which you as an NSX administrator can edit to fit your requirements. It is possible to create an installer with a predefined gateway address, an option to run it on system startup and a bunch of other settings. In this example, I will create a package for Windows, Linux and Mac, make it launch on startup, the SSL network adapter will be hidden and there will be a desktop icon.
Add an Installation Package
- Move from the “Private Networks” sub-menu to the “Installation Package” sub-menu.
- Click the ”+” icon at the top left to start adding a package.
- In the popup window, give the package a name, add the gateway address by clicking the ”+” icon, select for which operation system it is intended and select any other option you need. Click “OK” when you’re done.
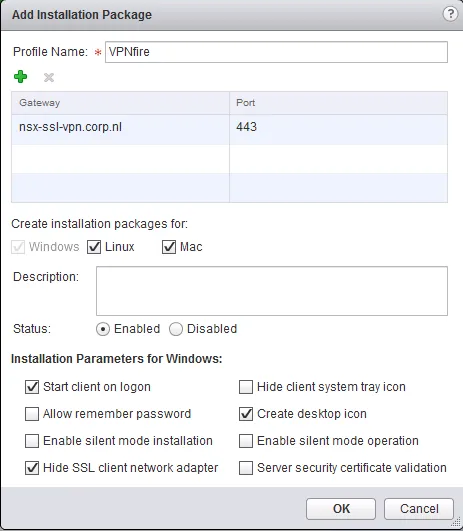
After building the installation package, adding a private network and IP Pool, adding an authentication method, you can go ahead and enable the SSL VPN-Plus service.
Enable the SSL VPN-Plus service
- Move from the “Installation package” sub-menu to the “Dashboard” sub-menu.
- Click the shiny “Enable” button to enable the service.
Once you’ve gone through all these steps, you should be able to browse to the portal via a browser, login, download the installer package, install it and login to your VPN.
 |  |
 | |
Implement Web Access SSL VPN-Plus
Requirements:
- Existing NSX Edge Services Gateway.
- SSL VPN-Plus service configured and enabled.
VMware Documentation: Configure Web Access SSL VPN-Plus
Web Access in SSL VPN-Plus is a way to share internal resources (CRM, Sharepoint data, other web applications) through the SSL VPN-Plus interface. A secured reverse proxy, if you will.
Adding a Web Resource
- Login to your vSphere Web Client.
- Navigate to “Networking & Security” and select the “NSX Edges” menu.
- Choose the NSX Edge you want to modify and select the “Manage” tab.
- Then select the “SSL VPN-Plus” sub-tab and select the “Web Resource” sub-menu.
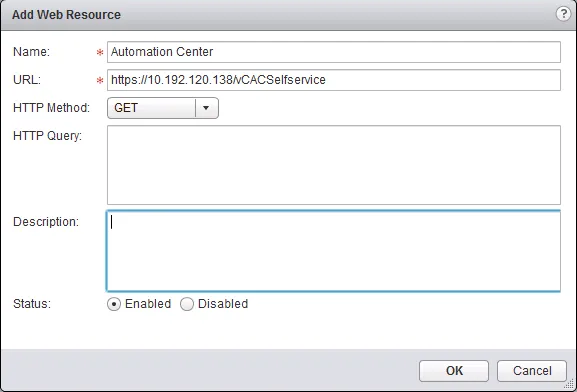
- Once there, click the ”+” icon to open the “Add Web Resource” popup window.
- Enter the resource name, the URL where it translates to and optionally select the HTTP method and query parameters and a description for the resource. Also decide to “Enable” or “Disable” it.
- Click “OK” when you’re done.
Enable/Disable L2 VPN
Requirements:
- Existing NSX Edge Services Gateway.
VMware Documentation: Enable L2 VPN
L2 VPNs (or Layer-2 VPNs) are VPN tunnels that extend the layer-2 domain (same subnet) across routed links. They can be established over a leased line or even the internet. They are mostly used for migration purposes and compute bursting. The next two chapters will show you how to configure a L2 VPN tunnel.
First, we need to enable the service.
Enable the Load Balancer service
- Login to your vSphere Web Client.
- Navigate to “Networking & Security” and select the “NSX Edges” menu.
- Choose the NSX Edge you want to modify and select the “Manage” tab.
- Then select the “VPN” sub-tab and select the “L2 VPN” sub-menu.
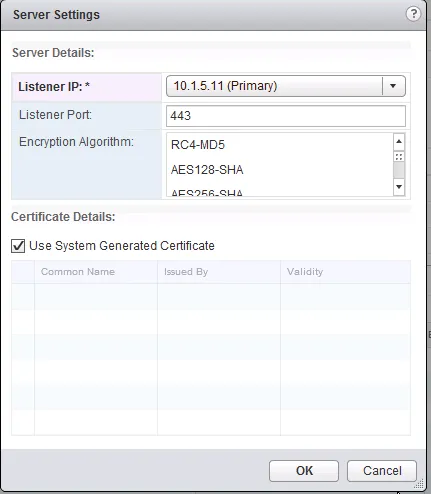
- First, set the listening IP address by clicking “Change” on the “Global Configuration Details” table.
- Select the “Listener IP” address, select the “Encryption Algorithm” and optional change the port number and select whether to use a self-signed certificate or a certificate you created earlier. Click “OK” when you’re done.
- Click the “Enable” button at the top of the page.
- Before clicking “Publish Changes” to activate the L2 VPN service, you’ll need to add a “Peer Site” which is described in the next chapter.
Add and configure a L2 VPN server
Requirements:
- Existing NSX Edge Services Gateway.
- Second NSX ESG to set up the L2 VPN with.
VMware Documentation: Add L2 VPN Server
After setting the Listener IP address, the L2 VPN server needs to be configured with “Peer Site”. This Peer Site basically contains the authentication and stretched interfaces.
Configure a L2 VPN Server
- (Assuming you’re still on the “L2 VPN” sub-menu).
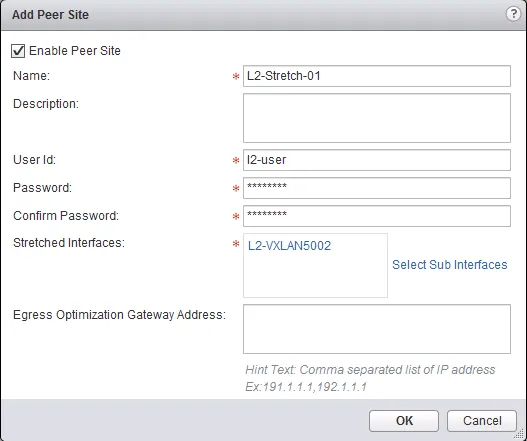
- Click the ”+” icon on the “Site Configuration Details” table.
- In the popup window, give the L2 VPN a name, optional description, an username and password for authentication and select the stretch interfaces (mind that only trunked interfaces are supported, so you have to have created one).
- Click “OK” when you’re done and click “Publish Changes” at the top of the page to enable the configuration you did in the last two chapters.
Add and configure a L2 VPN client
Requirements:
- Existing NSX Edge Services Gateway.
- Second NSX ESG configured as a L2 VPN Server.
VMware Documentation: Add L2 VPN Client
After setting up a L2 VPN Server, you can configure a ESG as a L2 VPN Client to create the VPN and bridge the network.
Configure a L2 VPN Client
-
Login to your vSphere Web Client.
-
Navigate to “Networking & Security” and select the “NSX Edges” menu.
-
Choose the NSX Edge you want to modify and select the “Manage” tab.
-
Then select the “VPN” sub-tab and select the “L2 VPN” sub-menu.
-
Click the “Enable” button at the top of the page.
-
Select “Client” radius in the “L2VPN Mode” selection.
-
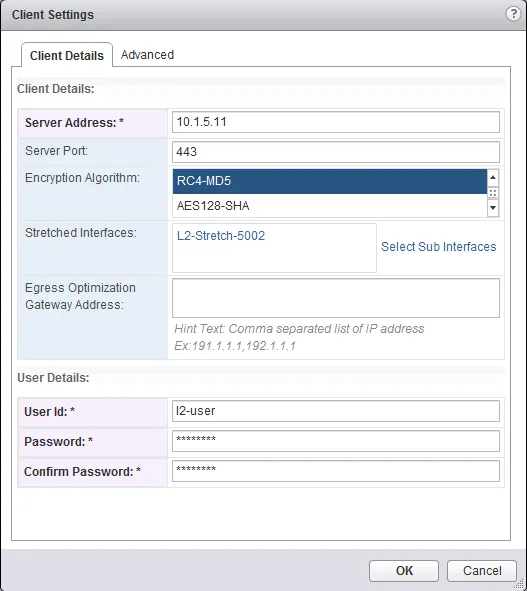
Click the “Change” button on the “Global Configuration Details” table.
-
In the popup window, enter the server IP address, select the port number and encryption algorithm (needs to match the servers) and select the stretch interface. Below enter the username and password details for authentication.
-
Click “OK” when you’re done.
-
Click “Publish Changes” to enable the configuration you just did.
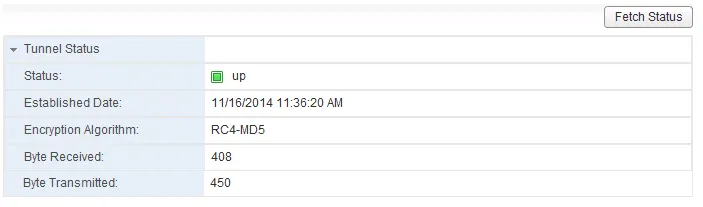
After setting up the L2 VPN Server and L2 VPN Client, possibly waiting a minute or so, you should get good news by clicking the “Fetch Status” button the L2 VPN Client or the “Show L2VPN Statistics” link on the L2 VPN Server. The client status should look like this: