API calls towards VMware Cloud are typically done using refresh tokens. Most examples you can find about the VMC API are around refresh tokens. These are personally bound to a VMC user. Which makes sense, you are doing something (creating an SDDC, or getting info, etc.). But, what if you're building a service against VMware Cloud and need all API calls not to be bound to an individual? That's where OAuth apps come in.
I wanted to document my tinkering to get an OAuth app to work and retrieving information around SDDCs, using that way of authentication.
Create OAuth App
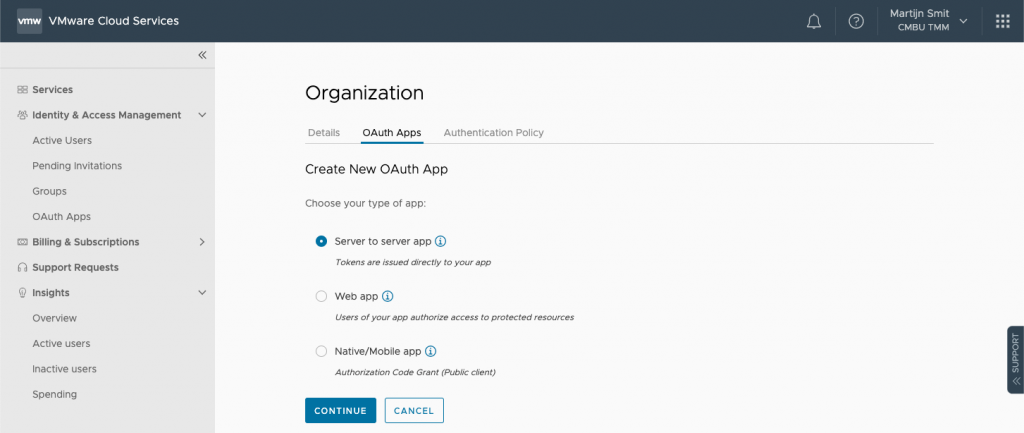
Head to the Cloud Services Portal and go to Organization -> OAuth Apps -> Create App. It will ask you what kind of OAuth app you'd like to create, with multiple possibilities. Have a look at the docs to get a sense of what type does what. For this exercise, I'll use a Server to server app. Imagine the application I'm building is a server-based application that polls VMC for information on intervals.
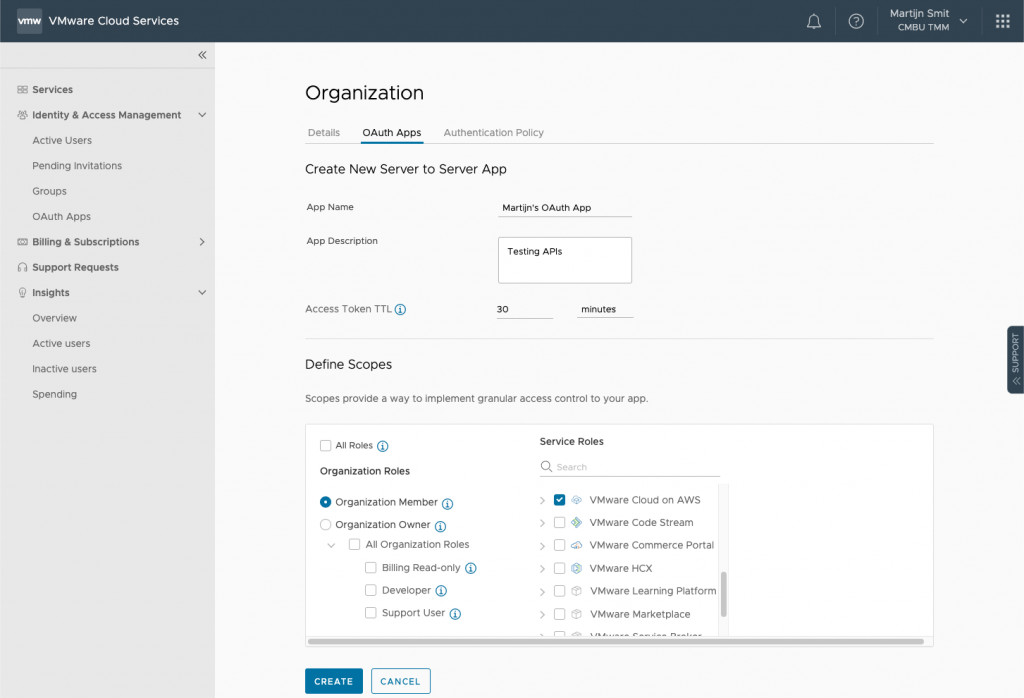
The next screen is all about giving the right permissions to the OAuth app. Make sure you give it the correct permissions from the start, as it's quite cumbersome to change them once the app has been created.
Also give it a friendly name, description, and time to live (TTL). The TTL defines how long the access token is valid when you authenticate with the app credentials.
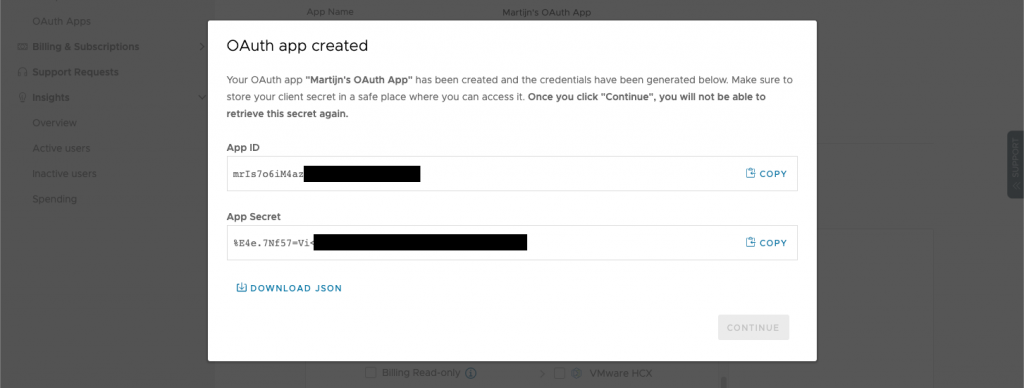
After creating the app, you'll be presented with the App ID and App Secret. Keep those in a safe place, you'll need them when talking to the API.
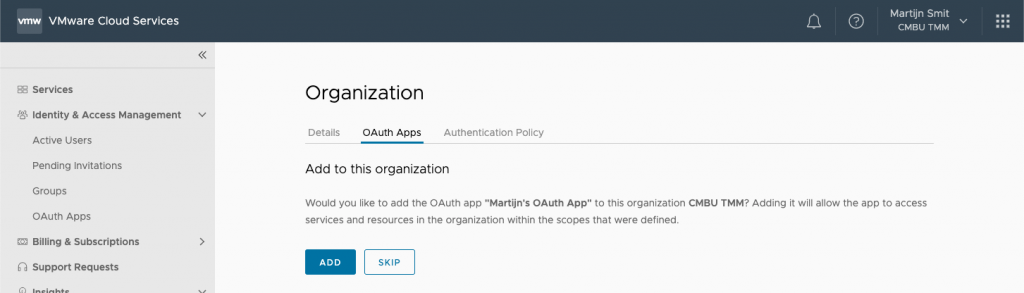
For the last step, add the new app to the organization. That'll effect the permissions you gave it earlier onto the organization (and it's services).
After adding it to the organization, you can start using it.
OAuth App to Access Token
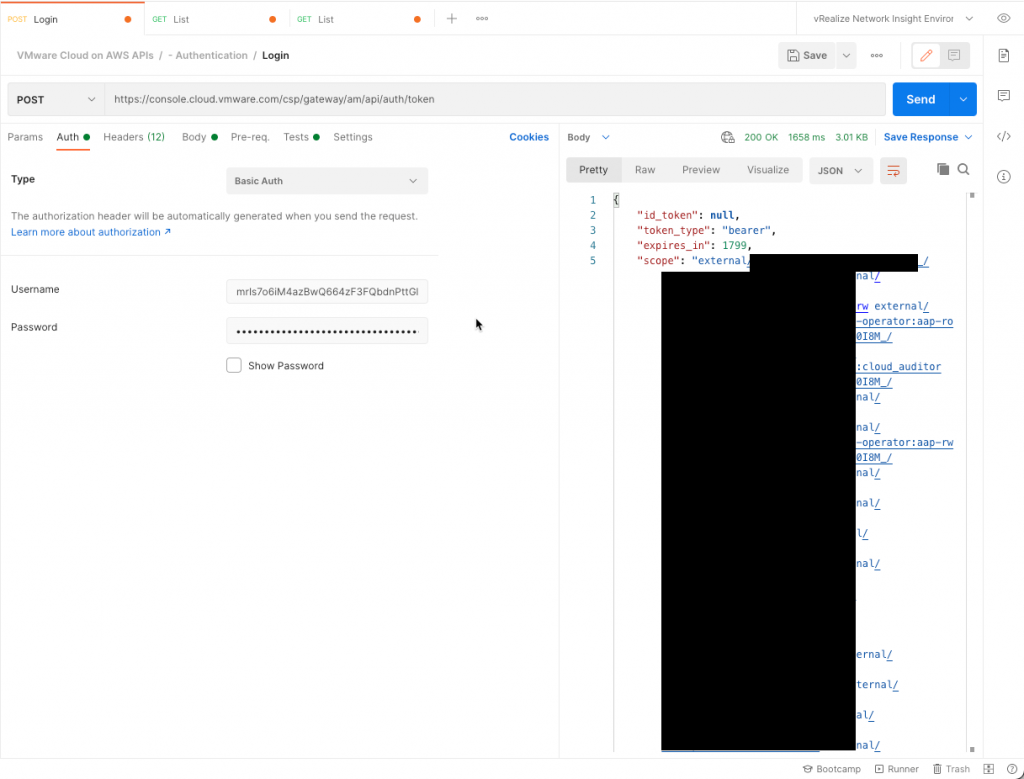
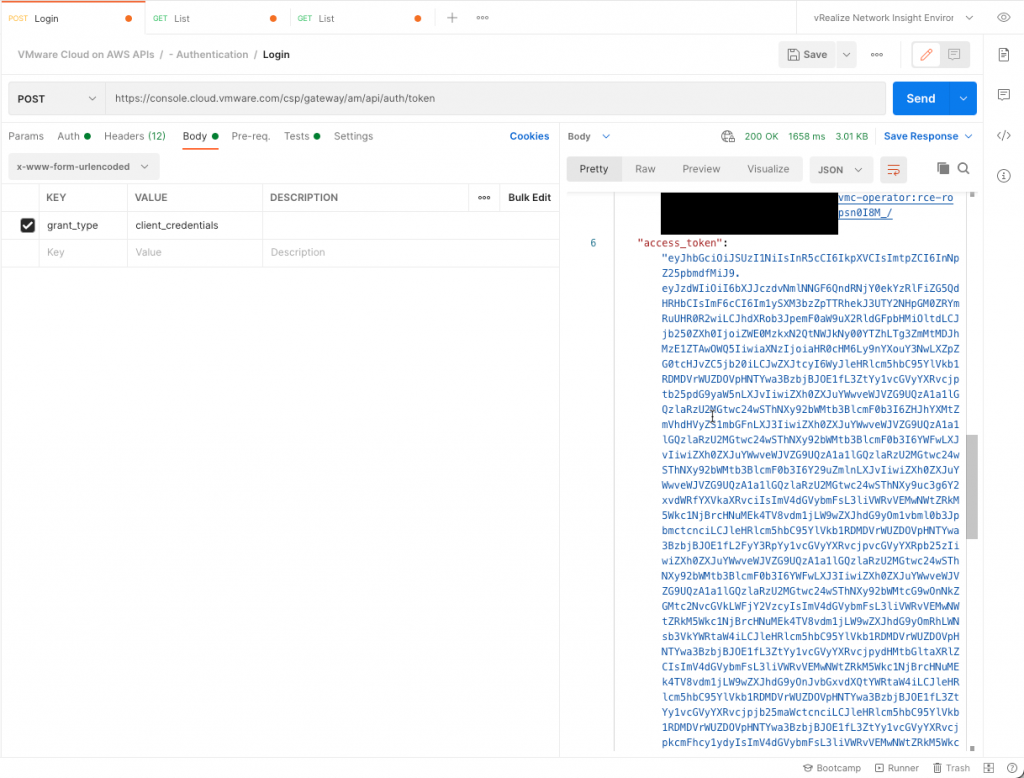
Just like with the refresh token, before you can do anything else; exchange the OAuth app credentials for an access token. We're going to do a POST API call to /csp/gateway/am/api/auth/token, saying we're using a client_credentials grant type and add basic authentication with the app ID and secret in it.
Use the app ID as the authentication username and app secret as the password. The body should be x-www-form-urlencoded with only 1 key called grant_type with value client_credentials.
If successful, the OAuth app credentials are exchanged for an access_token, which you can save and use it for sub sequential API calls.
Using the Access Token
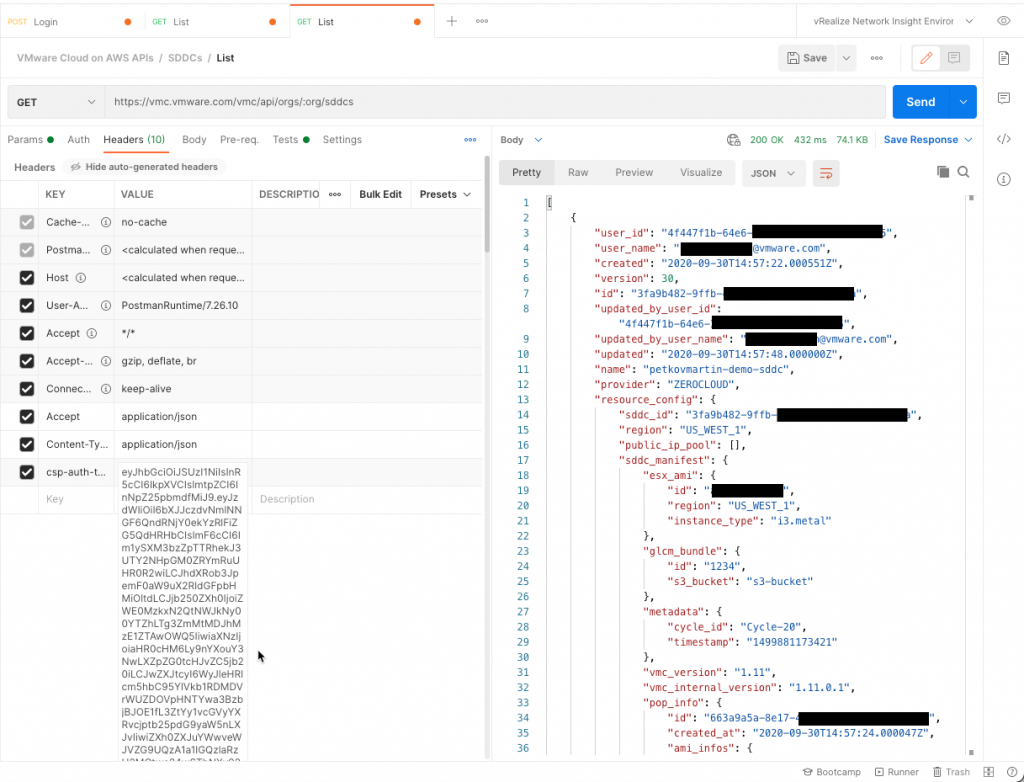
After getting the access token successfully, you can use it for the next API calls in the csp-auth-token header. This is no different than using a refresh token. Here's an example to get a list of SDDCs:

Leave a Reply