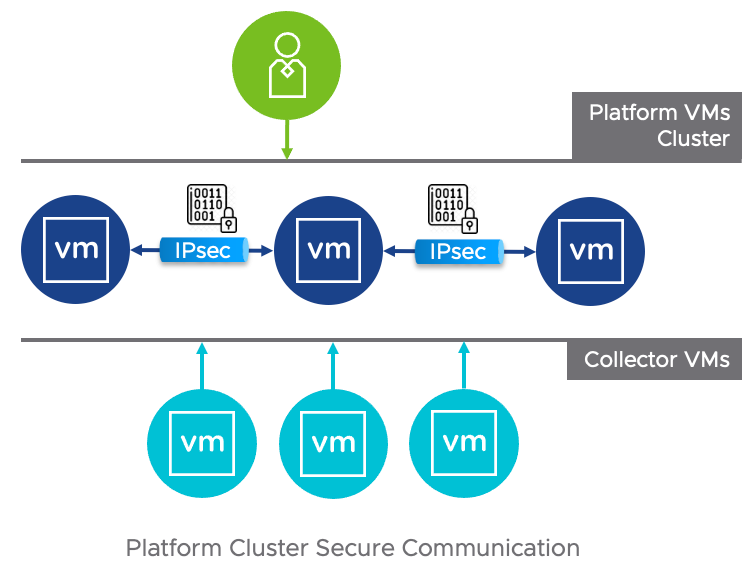
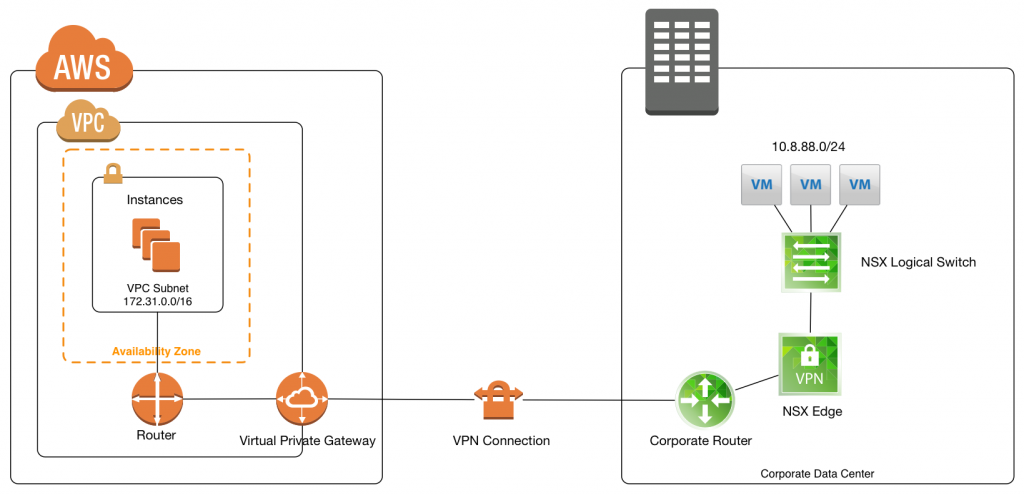
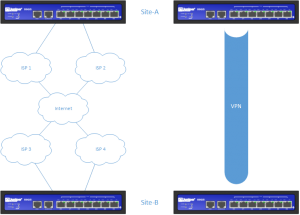
I'm always looking to simplify connectivity between my networks' different connections. With a home lab, colocated servers, and a few clouds that host projects, it's a web.
This was all connected with VPNs in the past, but everyone hates VPNs.
I moved to SD-WAN when VMware acquired VeloCloud, and I had the fortune to get a few SD-WAN edges. But I handed them back when I left VMware, so I also needed to update the connectivity.
Enter Tailscale.
Note: this is not a sponsored post. I just really, really like the product. 😃