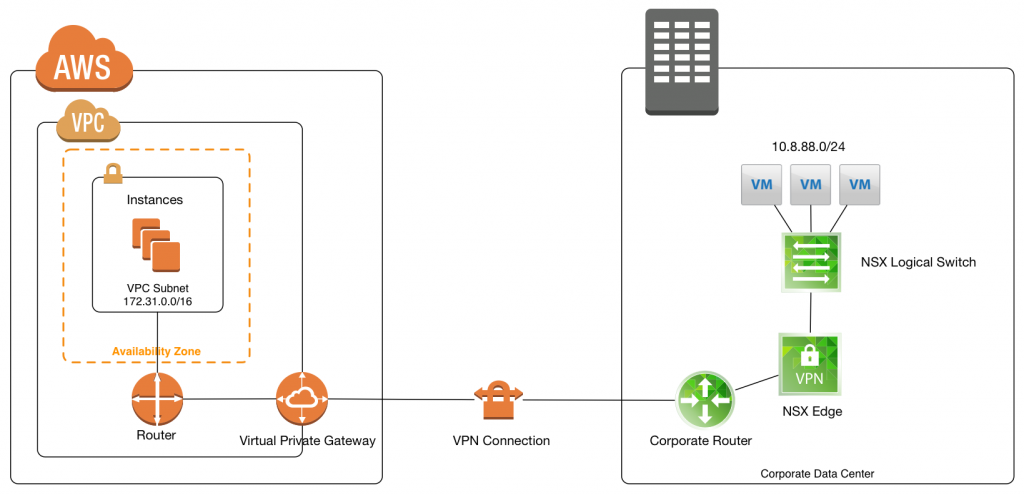
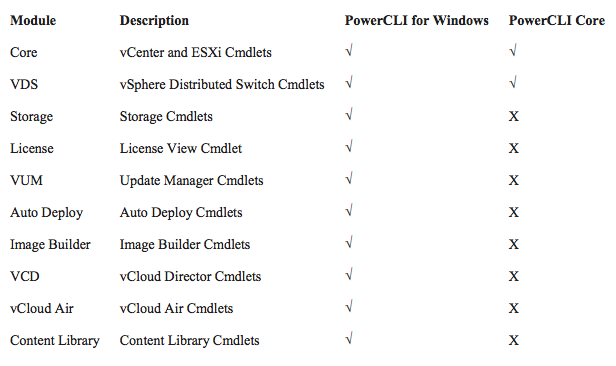
NSX 6.3 has just been made generally available and it's a humongous one. The changes in this new version reflect a new maturation phase in which NSX is now in. Here are my top picks, for the entire list of changes go here.
Controller Disconnect Operation (CDO) Mode
The control plane and data plane in SDN are inherently separated from each other. The control plane can be shut down without affecting the data plane, at least, affecting it immediately. Once the control plane is down, no changes can be made and the data plane operators (in NSXs case, the … Read more