IPv6 is here and IPv4 is definitely running out of time. Here in the Netherlands, the consumer internet providers have been "working on it" for years. I've been lobbying for IPv6 connectivity for years, without much luck. After a time of experimenting with IPv6-over-IPv4 tunnels and Teredo, I basically gave up on those technologies due to various reasons; high latency, complexity & subnet reputation (a lot of shady stuff was going on those free IPv6 subnets).
Recently, I finalized my IPv6 implementation in my hosted environment (couple of websites, other apps/databases), which also contains a NSX testlab. Considering I also have a NSX testlab at home, I started looking into stretching the IPv6 connectivity from the datacenter setup to my home. I already had an IPsec tunnel for management traffic, so I figured that this was the best place to start.
NSX has support for IPv6, but unfortunately it's not a full implementation. Most of the support is in the NSX Edge, the DLR doesn't have much support. The Edge & DFW have enough support to get you going, but there's some serious work that needs to be done. For instance: IPv6 inside an IPv4 IPsec tunnel is not supported by VMware. It seems to work, it's not officially supported. </disclaimer>
Design
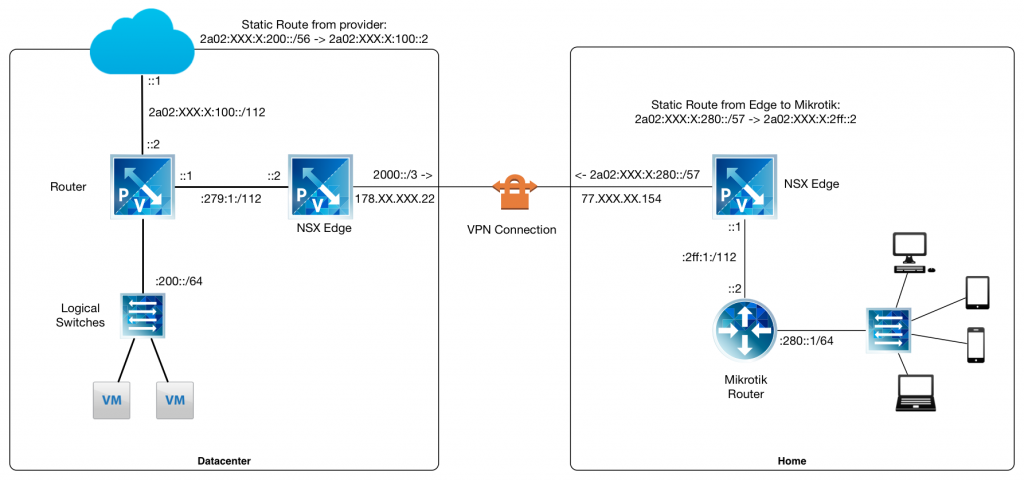
After a bit of back and forth with technical impossibilities, the design came out as following:
The internet provider in the datacenter supplied a /56 subnet which is statically routed from the provider to a datacenter router in a point-to-point /112 subnet. From there the /56 subnet is divided into two /57 subnets. One to be used locally and one to be used over the VPN. The local subnet is eventually divided up in /64 subnets to provide access to virtual machines.
There's a VPN between the NSX Edges which uses IPv4 as endpoints and routes IPv6 subnets over that VPN. Note: as the home network needs to use the datacenter network as it's default gateway, so you'd actually want to use ::/0. However, the NSX Edges does not seem to like that prefix. It breaks off the VPN connection after about 10 minutes, with no logging as to why. I found that if you use 2000::/3 (the global unicast space), the VPN connection will be stable. In the home network, there's a Mikrotik router which acts as the default gateway for all devices, which does fully support IPv6 and does Router Advertisements (RA), so that devices can use auto configuration for addresses.
IPv6 Configuration - Datacenter
Within NSX, create a NSX Edge and the required topology. I'm not going into details of those steps, you can check out my VCIX-NV Study Guide for step-by-step guidance.
Router
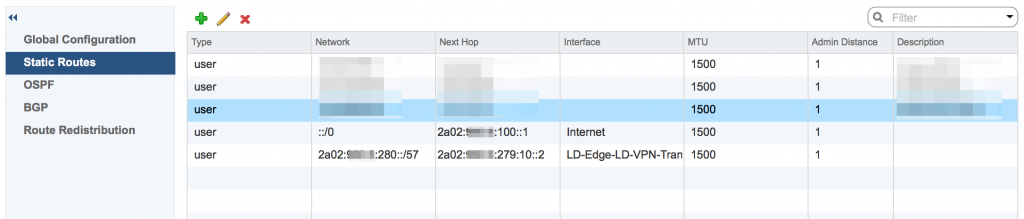
To start, we need the IPv6 subnet we're going to distribute through the VPN to be routed towards the NSX Edge that will be used for the VPN. Here's the route configuration for the datacenter router (happens to be a NSX Edge, can be different):
NSX Edge
The Edge we're going to use for the VPN only has a single IPv6 default route (::/0) towards it's neighbor, the datacenter router:
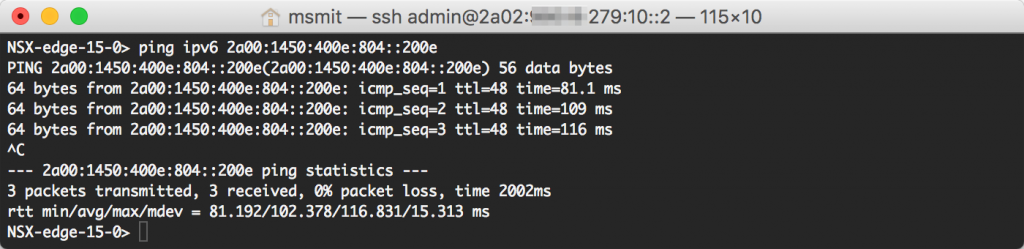
After the default IPv6 gateway is set, verify that you have IPv6 connectivity towards the internet. This is a ping towards google.com where I used the Ipv6 address instead of ‘google.com' due to lack of DNS servers:
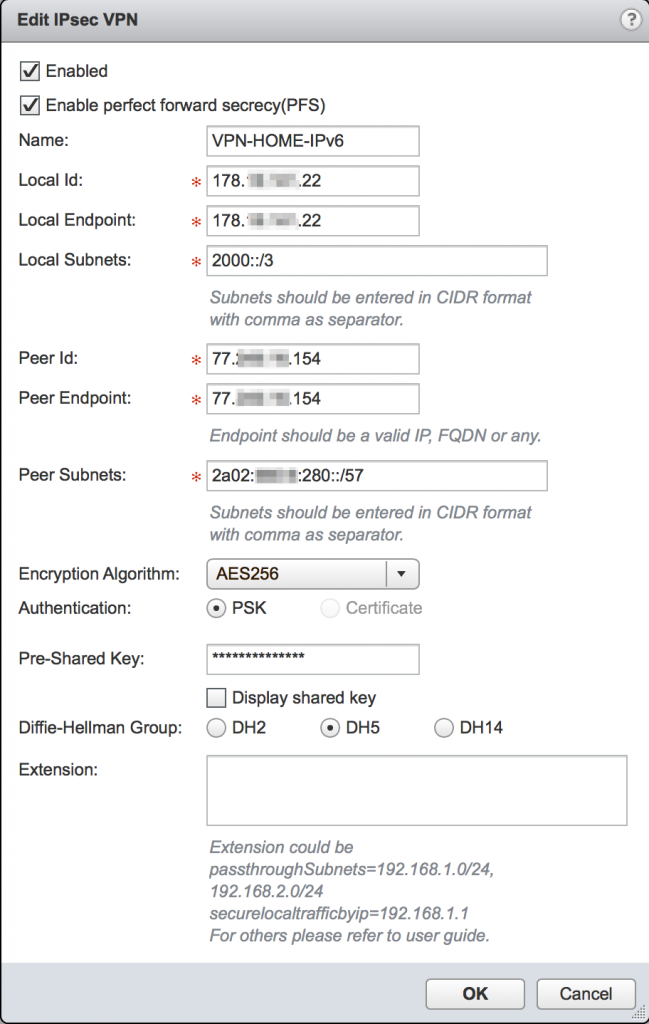
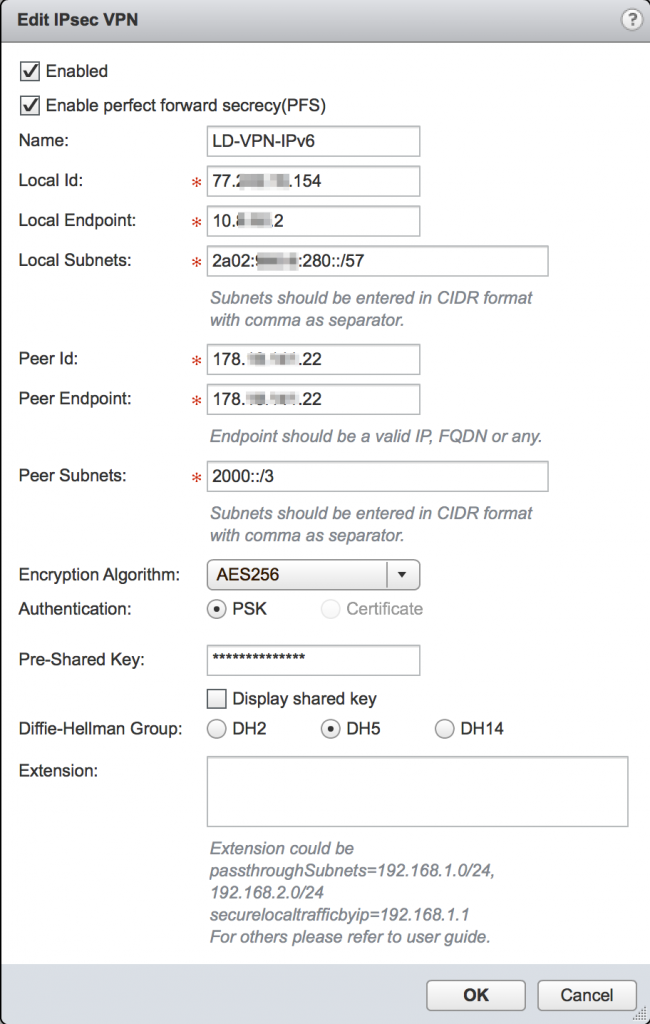
When the NSX Edge which will terminate the VPN has IPv6 connectivity, the VPN connection can be configured. Here we will use IPv4 endpoints, while the encrypted subnets will be IPv6. When you take that into account, the configuration details are pretty straightforward:
IPv6 Configuration - Home
Now we have the datacenter side all set up. In the home side, we will do exactly the same thing only reversed, with one big difference: no IPv6 default connectivity. Build a NSX Edge and make sure it can connect to the IPv4 endpoint on the datacenter side through the internet. My network routes the IPv6 subnet forward to a Mikrotik, but you could also just attach the Edge to the devices network.
Note: If you do connect devices directly to the Edge, please note that you have to use static addressing on your devices, there is no IPv6 address auto configuration on the Edge. This is why I used a Mikrotik.
NSX Edge
Below is the VPN configuration used on the home side:
Note: the Local Endpoint here is an internal IP address, as the home NSX Edge is not directly connected to the internet and goes through a NAT gateway.
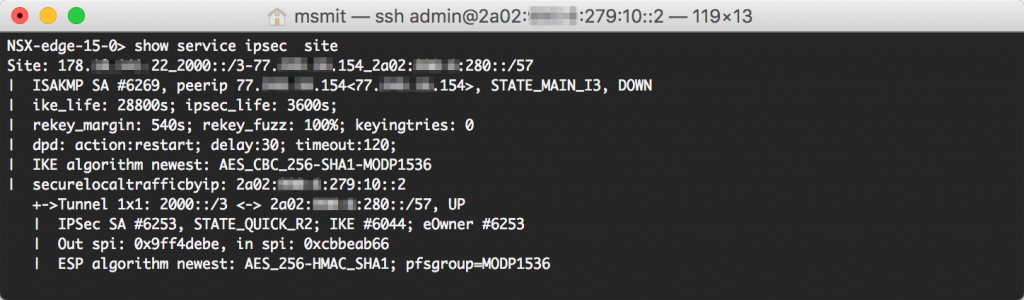
After configuring the VPN on both sides, the VPN should come online - which you can check on either of your NSX Edges:
When the VPN connection is online, configure a network with an IPv6 /64 subnet and put something in there (your laptop, a test VM, whatever supports IPv6). Why a /64? Because auto configuration uses your MAC address for the IPv6 address generation and a MAC address is 64bits (IPv6 = 128 bits).
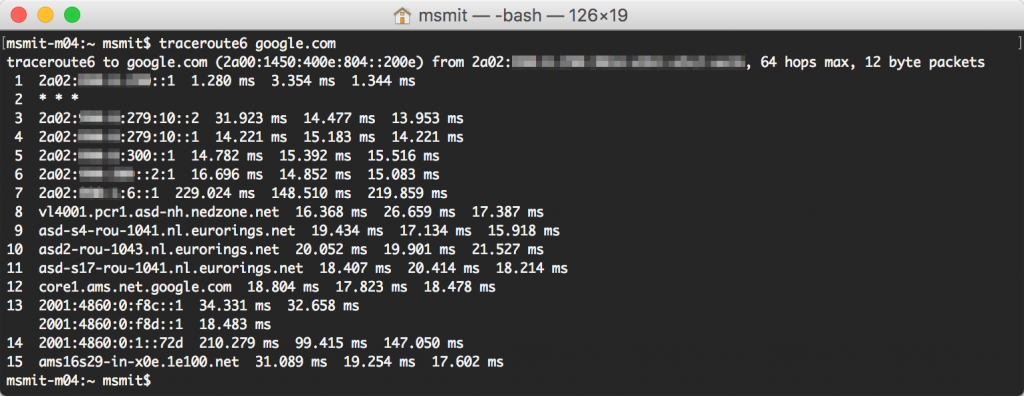
Now that you have a IPv6 over IPv4 VPN running and have connected your laptop to the IPv6 subnet inside your home, try to connect through the IPv6 version of google.com:
You can see the route going through the local IPv6 router, then through the NSX Edge on the home side (that's the timeout) and on through the datacenter IPv6 network towards the internet.
I'm fully aware that not everyone has a NSX implementation (or even a testlab) at home to use for this, but the NSX Edge also works with different kinds of VPN devices, so you're not necessarily limited to using NSX on both sides.

Leave a Reply